The now-patched vulnerability could have allowed remote attackers to bypass authentication and take over targeted users' accounts on third-party services and apps that have been registered using 'Sign in with Apple' option.
Launched last year at Apple's WWDC conference, 'Sign in with Apple' feature was introduced to the world as a privacy-preserving login mechanism that allows users to sign up an account with 3rd-party apps without disclosing their actual email addresses (also used as Apple IDs).
In an interview with The Hacker News, Bhavuk Jain revealed that the vulnerability he discovered resided in the way Apple was validating a user on the client-side before initiating a request from Apple's authentication servers.
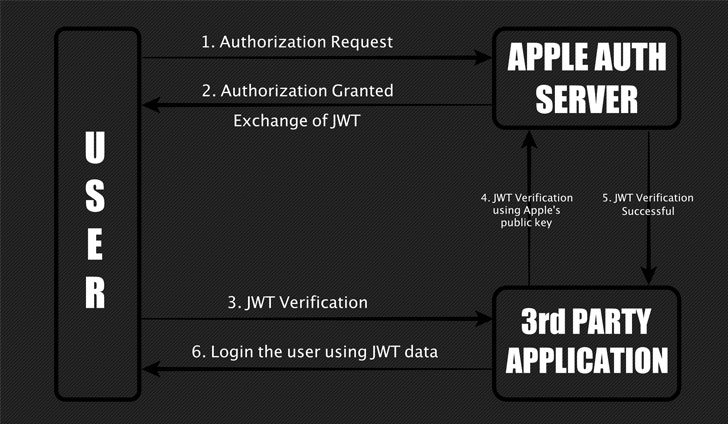
For those unaware, while authenticating a user via 'Sign in with Apple,' the server generates JSON Web Token (JWT) containing secret information that third-party application uses to confirm the identity of the signing-in user.
Bhavuk found that though Apple asks users to log in to their Apple account before initiating the request, it was not validating if the same person is requesting JSON Web Token (JWT) in the next step from its authentication server.
Therefore, the missing validation in that part of the mechanism could have allowed an attacker to provide a separate Apple ID belonging to a victim, tricking Apple servers into generating JWT payload that was valid to sign in into a 3rd-party service with the victim's identity.
"I found I could request JWTs for any Email ID from Apple, and when the signature of these tokens was verified using Apple's public key, they showed as valid. This means an attacker could forge a JWT by linking any Email ID and gaining access to the victim's account," Bhavuk said.
The researcher confirmed The Hacker News that the vulnerability worked even if you choose to hide your email ID from the 3rd-party services and can also be exploited to sign up a new account with the victim's Apple ID.
"The impact of this vulnerability was quite critical as it could have allowed a full account takeover. Many developers have integrated Sign in with Apple since it is mandatory for applications that support other social logins. To name a few that use Sign in with Apple - Dropbox, Spotify, Airbnb, Giphy (now acquired by Facebook)," Bhavuk added.
Though the vulnerability existed on the Apple side of code, the researcher said it's possible that some services and app offering 'Sign in with Apple' to their users might have already been using a second factor of authentication that could mitigate the issue for their users.
Bhavuk responsibly reported the issue to the Apple security team last month, and the company has now patched the vulnerability.
Besides paying bug bounty to the researcher, in response, the company also confirmed that it did an investigation of their server logs and found the flaw was not exploited to compromise any account.
THN
#osutayusuf
- Get link
- X
- Other Apps
- Get link
- X
- Other Apps

Comments
Post a Comment