
A high-severity series of four vulnerabilities can allow remote adversaries to gain arbitrary code execution in the pre-boot environment on Dell devices, researchers said. They affect an estimated 30 million individual Dell endpoints worldwide.
According to an analysis from Eclypsium, the bugs affect 129 models of laptops, tablet and desktops, including enterprise and consumer devices, that are protected by Secure Boot. Secure Boot is a security standard aimed at making sure that a device boots using only software that is trusted by the device original equipment manufacturer (OEM), to prevent rogue takeovers.
The bugs allow privileged network adversaries to circumvent Secure Boot protections, control the device’s boot process, and subvert the operating system and higher-layer security controls, researchers at Eclypsium said on Thursday. They carry a cumulative CVSS score of 8.3 out of 10.
“Technology vendors of all types are increasingly implementing over-the-air update processes to make it as easy as possible for their customers to keep their firmware up to date and recover from system failures,” researchers noted in an analysis. “And while this is a valuable option, any vulnerabilities in these processes, such as those we’ve seen here in Dell’s BIOSConnect, can have serious consequences.”Specifically, the issues affect the BIOSConnect feature within Dell SupportAssist (a technical support solution that comes preinstalled on most Windows-based Dell machines). BIOSConnect is used to perform remote OS recoveries or to update the firmware on the device.
The report noted that the specific vulnerabilities allow an attacker to remotely exploit the UEFI firmware of a host and gain control over the most privileged code on the device.
“This combination of remote exploitability and high privileges will likely make remote update functionality an alluring target for attackers in the future,” the report concluded.
Insecure TLS Connection: Impersonating Dell
The first vulnerability (CVE-2021-21571) is the beginning of a chain that can lead to remote code execution (RCE).
When BIOSConnect attempts to connect to the backend Dell HTTP server to perform a remote update or recovery, it enables the system’s BIOS (the firmware used to perform hardware initialization during the booting process) to reach out to Dell backend services over the internet. Then, it coordinates an update or recovery process.
The issue is that the TLS connection used to connect BIOS to the backend servers will accept any valid wildcard certificate, Eclypsium researchers said. So, an attacker with a privileged network position can intercept that connection, impersonate Dell and deliver attacker-controlled content back to the victim device.
“The process of verifying the certificate for dell.com is done by first retrieving the DNS record from the hard-coded server 8.8.8.8, then establishing a connection to [Dell’s download site],” according to the analysis. “However, any valid wildcard certificate issued by any of the built-in Certificate Authorities contained within the BIOSConnect feature in BIOS will satisfy the secure connection condition, and BIOSConnect will proceed to retrieve the relevant files. The bundle of CA root certificates in the BIOS image was sourced from Mozilla’s root certificate file (certdata.txt).”
Overflow Vulnerabilities Enabling Arbitrary Code Execution
Once this first “gatekeeper” bug is exploited to deliver malicious content back to the victim machine, attackers then have a choice of three distinct and independent overflow vulnerabilities (CVE-2021-21572, CVE-2021-21573, CVE-2021-21574), any of which can be used to gain pre-boot RCE on the target device, researchers said.
Two of the vulnerabilities affect the OS recovery process, while the third affects the firmware update process, according to Eclypsium, which isn’t releasing further technical details yet.
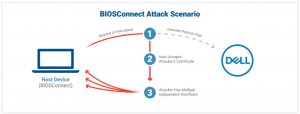
The attack scenario: Click to enlarge. Source: Eclypsium
Any attack scenario would require an attacker to be able to redirect the victim’s traffic, such as via a machine-in-the-middle (MITM) attack – something that’s not much of a barrier, researchers said.
“Machine-in-the-middle attacks are a relatively low bar to sophisticated attackers, with techniques such as ARP spoofing and DNS cache poisoning being well-known and easily automated,” according to the report. “Additionally, enterprise VPNs and other network devices have become a top target of attackers, and flaws in these devices can allow attackers to redirect traffic. And finally, end-users working from home are increasingly reliant on SOHO networking gear. Vulnerabilities are quite common in these types of consumer-grade networking devices and have been exploited in widespread campaigns.”
The groundwork effort to carry out an attack is likely a positive tradeoff for cybercriminals, given that a successful compromise of the BIOS of a device would allow attackers to establish ongoing persistence while controlling the highest privileges on the device. This is because they would control the process of loading the host operating system, and would be able to disable protections in order to remain undetected, the report noted.
“The virtually unlimited control over a device that this attack can provide makes the fruit of the labor well worth it for the attacker,” Eclypsium researchers said.
Dell Issues Patches
Dell has now pushed out patches for BIOS on all of the affected systems. For details, refer to its advisory.
“It is advisable to run the BIOS update executable from the OS after manually checking the hashes against those published by Dell,” Eclypsium recommended, rather than relying on BIOSConnect to apply BIOS updates.
Comments
Post a Comment