More than six years after Facebook launched its ambitious Free Basics program to bring the Internet to the masses, the social network is back at it again with a new zero-rating initiative called Discover.
The service, available as a mobile web and Android app, allows users to browse the Internet using free daily data caps.
Facebook Discover is currently being tested in Peru in partnership with local telecom companies such as Bitel, Claro, Entel, and Movistar.
Unlike the regular rich-content browsing, Facebook's latest connectivity project only provides low-bandwidth text-only based browsing, meaning other forms of data-intensive content such as audio and video are not supported.
Another key differentiator is that it treats all websites equally, whereas users of Free Basics are limited to a handful of sites that are submitted by developers and meet technical criteria set by Facebook.
Facebook Discover is currently being tested in Peru in partnership with local telecom companies such as Bitel, Claro, Entel, and Movistar.
Unlike the regular rich-content browsing, Facebook's latest connectivity project only provides low-bandwidth text-only based browsing, meaning other forms of data-intensive content such as audio and video are not supported.
Another key differentiator is that it treats all websites equally, whereas users of Free Basics are limited to a handful of sites that are submitted by developers and meet technical criteria set by Facebook.
The move, ultimately, drew criticism for violating principles of net neutrality, leading to its ban in India in 2016.
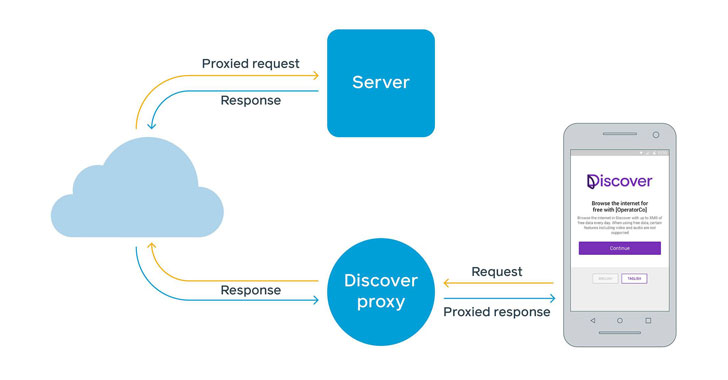
But how does Discover actually work? It's a lot similar to Free Basics in that all traffic is routed through a proxy As a result, the device only interacts with the proxy servers, which acts as a "client" to the website users have requested for.
This web-based proxy service runs within a whitelisted domain under "freebasics.com" that the operator makes the service available for free (e.g. "https://example.com" is rewritten as "https://https-example-com.0.freebasics.com"), which then fetches the webpages on behalf of the user and deliver them to their device.
"There is extensive server-side logic in place to make sure links and hrefs are correctly transformed," the company said. "This same logic helps ensure that even HTTP-only sites are delivered securely over HTTPS on Free Basics between the client and the proxy."
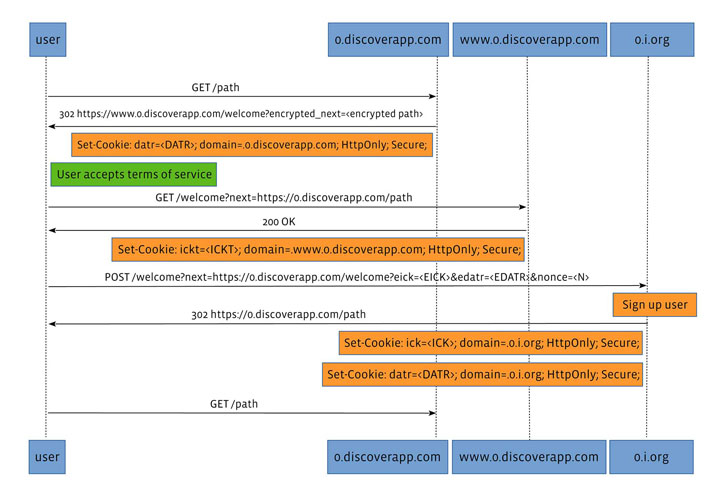
In addition, the cookies used by the websites are stored in an encrypted fashion on the server to prevent mobile browsers from hitting cookie storage limits. The encryption key (called internet cookie key or "ick") is stored on the client so that the contents of the key cannot be read without knowing the user's key.
"When the client provides the ick, it is forgotten by the server in each request without ever being logged," Facebook noted.
A Secure Web-Based Proxy.
But how does Discover actually work? It's a lot similar to Free Basics in that all traffic is routed through a proxy As a result, the device only interacts with the proxy servers, which acts as a "client" to the website users have requested for.
This web-based proxy service runs within a whitelisted domain under "freebasics.com" that the operator makes the service available for free (e.g. "https://example.com" is rewritten as "https://https-example-com.0.freebasics.com"), which then fetches the webpages on behalf of the user and deliver them to their device.
"There is extensive server-side logic in place to make sure links and hrefs are correctly transformed," the company said. "This same logic helps ensure that even HTTP-only sites are delivered securely over HTTPS on Free Basics between the client and the proxy."
In addition, the cookies used by the websites are stored in an encrypted fashion on the server to prevent mobile browsers from hitting cookie storage limits. The encryption key (called internet cookie key or "ick") is stored on the client so that the contents of the key cannot be read without knowing the user's key.
"When the client provides the ick, it is forgotten by the server in each request without ever being logged," Facebook noted.
But allowing JavaScript content from third-party websites also opens up avenues for attackers to inject malicious code, and worse, even lead to session fixation.
To mitigate this attack, Facebook Discover makes use of an authentication tag (called "ickt") that's derived from the encryption key and a second browser identifier cookie (named "datr"), which is stored on the client.
The tag, which is embedded in every proxy response, is then compared with the 'ickt' on the client-side to check for any signs of tampering. If there's a mismatch, the cookies are deleted. It also makes use of a "two-frame solution" that embeds the third-party site within an iframe that's secured by an outer frame, which makes use of the aforementioned tag to ensure the integrity of the content.
But for websites that disable the loading of the page in a frame to counter clickjacking attacks, Discover works by removing that header from the HTTP response, but not before validating the inner frame.
Furthermore, to prevent impersonation of the Discover domain by phishing sites, the service blocks navigation attempts to such links by sandboxing the iframe, thus preventing it from executing untrusted code.
"This architecture has been through substantial internal and external security testing," Facebook's engineering team concluded. "We believe we have developed a design that is robust enough to resist the types of web application attacks we see in the wild and securely deliver the connectivity that is sustainable for mobile operators."
To mitigate this attack, Facebook Discover makes use of an authentication tag (called "ickt") that's derived from the encryption key and a second browser identifier cookie (named "datr"), which is stored on the client.
The tag, which is embedded in every proxy response, is then compared with the 'ickt' on the client-side to check for any signs of tampering. If there's a mismatch, the cookies are deleted. It also makes use of a "two-frame solution" that embeds the third-party site within an iframe that's secured by an outer frame, which makes use of the aforementioned tag to ensure the integrity of the content.
But for websites that disable the loading of the page in a frame to counter clickjacking attacks, Discover works by removing that header from the HTTP response, but not before validating the inner frame.
Furthermore, to prevent impersonation of the Discover domain by phishing sites, the service blocks navigation attempts to such links by sandboxing the iframe, thus preventing it from executing untrusted code.
"This architecture has been through substantial internal and external security testing," Facebook's engineering team concluded. "We believe we have developed a design that is robust enough to resist the types of web application attacks we see in the wild and securely deliver the connectivity that is sustainable for mobile operators."
THN
#osutayusuf
- Get link
- X
- Other Apps
- Get link
- X
- Other Apps

Comments
Post a Comment