I see this gap manifesting in two ways. First, companies that want to hire cybersecurity talent simply cannot find candidates with sufficient skills. Second, companies that cannot afford specialized cybersecurity talent and therefore lack the necessary skills to adequately protect their organizations from the growing and increasingly sophisticated cyber threats.
Both of these are real problems, and both can lead to devastating consequences. It's also fair to say that most cybersecurity teams today are overworked and understaffed.
One of the primary reasons we need such high-level cybersecurity skills lies in the shortcomings of cybersecurity technologies. Due to the changing and increasingly sophisticated stream of attack techniques, the breadth and depth of cybersecurity defensive technologies used to combat these threats and protect organizations against breaches have exploded. Today, there seems to be a specialized tool to cover every part of the attack surface and response process.
Unfortunately, all but the largest organizations with the deepest pockets can afford to acquire and then adequately integrate and maintain the expansive set of technologies required to protect modern-day organizations from breaches. Most smaller companies suffer from a lack of technologies to protect their organizations.
We are in dire need of approaches that simplify and consolidate the cybersecurity toolset so that companies can afford the coverage required and to make effective breach protection accessible to those other than world-class experts.
Enter Cynet.
One company that seems to get the need for simplification, without sacrificing the effectiveness, is Cynet.
Cynet was formed specifically to consolidate multiple threat prevention and detection controls into a single offering for two primary reasons. First, keeping all the controls on a single platform allows for far better results than integrating and managing technologies from multiple providers.
Second, it dramatically simplifies the technology stack (not to mention affordability improvements). Then, Cynet goes beyond these benefits by automating many of the common workflows required to respond to cyber threats that would otherwise require high-level skills, time, and effort.
The Cynet 360 platform is built on three pillars; Extended Detection and Response (XDR), Response Automation, and Managed Detection and Response (MDR). These three components together provide what Cynet calls Autonomous Breach Protection - essentially breach protection on auto-pilot. Let's look at each of these components.
While XDR is considered a new technology – it's something Cynet has been doing since its inception. XDR technology essentially combines signals from multiple control points as part of a single platform to provide better results than when deploying multiple siloed controls and then trying to figure out the stream of alerts and data from each. Many analyst firms are touting XDR as "the next big thing in cybersecurity."
The Cynet XDR combines prevention, detection, and data from:
Cynet automates many tasks associated with threat detection response and cross-environment remediation, including infected hosts, compromised user accounts, malicious processes, and attacker-controlled network traffic.
Cynet's new Incident Engine can immediately improve cybersecurity operations for any company and help full the cybersecurity skills gap.
Many solutions can detect threats and then automatically prevent them from executing and causing damage. This is wonderful and helpful, but only represents the first step in addressing a threat. We must assume that the threat discovered is likely only the tip of the iceberg and is likely only a piece of a larger, coordinated attack. This is where the cybersecurity skill gap becomes dangerous.
The Cynet Incident Engine triggers an automated investigation following certain high-risk alerts, fully disclosing its root cause and scope, and applying all the required remediation activities. This is offered on a single platform, out of the box, ready to bring your cybersecurity to the next level on day one. This, my friends, is the most amazing and useful cybersecurity breakthrough I've seen in some time.
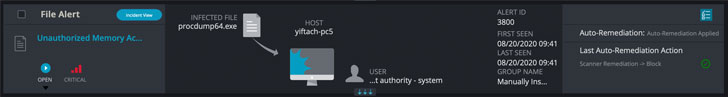
On certain high-risk alerts, customers can click the Incident View button:
This leads to a page that displays the full set of investigation steps and remediation actions that the Incident Engine performed as soon as the threat was detected.
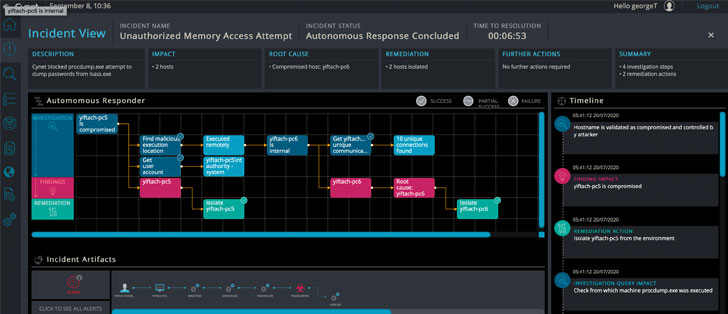
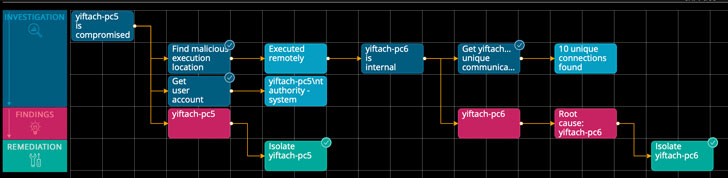
As shown in the screenshot below, a simple workflow diagram shows the series of investigation queries and results (blue) that lead to findings (red) that are addressed with remediation (green). The Timeline on the right shows a more detailed description of every step, while the Incident Artifacts display the attack flow. The full incident is summarized in the upper text boxes.
In the following example, we see an Unauthorized Memory Access Attempt alert that was triggered by an attempt to dump credentials – a common attack scenario. The initial alert indicates that Cynet neutralized the attempt and that the credentials were not accessed. The Incident Engine then does its thing - it isolates the compromised host against from which the attack was launched and revealed a lateral movement. It turns out that the attack was actually launched remotely from another host in the environment, which is the true root cause. This finding is concluded by isolating the root cause host as well.
This off-the-shelf automated root cause analysis, impact investigation, and remediation actions took Cynet's platform just under seven minutes to fully perform, all in the background, saving literally hours of analyst effort. Or, it performed a series of tasks to find and remediate threats that some organizations would not have known were necessary or how to do them.
Cynet calls their MDR team of cybersecurity experts CyOps. I find it amazing that Cynet includes 24x7 monitoring for all clients to ensure any real attacks are not overlooked. They also provide ad-hoc threat investigations and forensic analysis and guide their clients through any necessary remediation steps. CyOps is automatically included in the Cynet platform – at no additional cost.
This type of service is typically quite expensive and oftentimes only available from third-party providers. With CyOps intimate understanding of the Cynet platform, they can provide far superior service than MDR teams that some vendors contract with to support their platform.
The fully automated Incident Engine, coupled with Cynet's full Extended Detection and Response (XDR) platform and included Managed Detection and Response (MDR) service, provides quite a cyber protection package for any organization.
Many companies continue to rely solely on EDR or a combination of EDR and NGAV to protect the organization from cyberattacks and breaches. Alternatively, Cynet's solution provides a complete prevention and detection capability along with fully automated response actions and a full 24x7 MDR service to boot. If I were suffering from a lack of cybersecurity resources, as most companies are, my first call to improve my situation would be to Cynet.
Second, it dramatically simplifies the technology stack (not to mention affordability improvements). Then, Cynet goes beyond these benefits by automating many of the common workflows required to respond to cyber threats that would otherwise require high-level skills, time, and effort.
Product Review: Cynet 360, 2020 Fall Platform Update
The Cynet 360 platform is built on three pillars; Extended Detection and Response (XDR), Response Automation, and Managed Detection and Response (MDR). These three components together provide what Cynet calls Autonomous Breach Protection - essentially breach protection on auto-pilot. Let's look at each of these components.
XDR
While XDR is considered a new technology – it's something Cynet has been doing since its inception. XDR technology essentially combines signals from multiple control points as part of a single platform to provide better results than when deploying multiple siloed controls and then trying to figure out the stream of alerts and data from each. Many analyst firms are touting XDR as "the next big thing in cybersecurity."
The Cynet XDR combines prevention, detection, and data from:
- Endpoint Protection – Next-Generation Antivirus (NGAV) for basic endpoint malware prevention and detection and Endpoint Detection and Response (EDR) for more advanced endpoint protection, detection, and response,
- Network Traffic Analysis (NTA) for identifying malicious activity on your network,
- Entity and User Behavior Monitoring (EUBA) to detect anomalous user behaviors,
- Deception technology to trick successful intruders into exposing their presence before damage can be done.
Response Automation.
Cynet automates many tasks associated with threat detection response and cross-environment remediation, including infected hosts, compromised user accounts, malicious processes, and attacker-controlled network traffic.
The New Cynet Incident Engine.
Cynet's new Incident Engine can immediately improve cybersecurity operations for any company and help full the cybersecurity skills gap.
Many solutions can detect threats and then automatically prevent them from executing and causing damage. This is wonderful and helpful, but only represents the first step in addressing a threat. We must assume that the threat discovered is likely only the tip of the iceberg and is likely only a piece of a larger, coordinated attack. This is where the cybersecurity skill gap becomes dangerous.
The Cynet Incident Engine triggers an automated investigation following certain high-risk alerts, fully disclosing its root cause and scope, and applying all the required remediation activities. This is offered on a single platform, out of the box, ready to bring your cybersecurity to the next level on day one. This, my friends, is the most amazing and useful cybersecurity breakthrough I've seen in some time.
How it Works.
On certain high-risk alerts, customers can click the Incident View button:
This leads to a page that displays the full set of investigation steps and remediation actions that the Incident Engine performed as soon as the threat was detected.
As shown in the screenshot below, a simple workflow diagram shows the series of investigation queries and results (blue) that lead to findings (red) that are addressed with remediation (green). The Timeline on the right shows a more detailed description of every step, while the Incident Artifacts display the attack flow. The full incident is summarized in the upper text boxes.
In the following example, we see an Unauthorized Memory Access Attempt alert that was triggered by an attempt to dump credentials – a common attack scenario. The initial alert indicates that Cynet neutralized the attempt and that the credentials were not accessed. The Incident Engine then does its thing - it isolates the compromised host against from which the attack was launched and revealed a lateral movement. It turns out that the attack was actually launched remotely from another host in the environment, which is the true root cause. This finding is concluded by isolating the root cause host as well.
This off-the-shelf automated root cause analysis, impact investigation, and remediation actions took Cynet's platform just under seven minutes to fully perform, all in the background, saving literally hours of analyst effort. Or, it performed a series of tasks to find and remediate threats that some organizations would not have known were necessary or how to do them.
MDR - CyOps
Cynet calls their MDR team of cybersecurity experts CyOps. I find it amazing that Cynet includes 24x7 monitoring for all clients to ensure any real attacks are not overlooked. They also provide ad-hoc threat investigations and forensic analysis and guide their clients through any necessary remediation steps. CyOps is automatically included in the Cynet platform – at no additional cost.
This type of service is typically quite expensive and oftentimes only available from third-party providers. With CyOps intimate understanding of the Cynet platform, they can provide far superior service than MDR teams that some vendors contract with to support their platform.
Summary
The fully automated Incident Engine, coupled with Cynet's full Extended Detection and Response (XDR) platform and included Managed Detection and Response (MDR) service, provides quite a cyber protection package for any organization.
Many companies continue to rely solely on EDR or a combination of EDR and NGAV to protect the organization from cyberattacks and breaches. Alternatively, Cynet's solution provides a complete prevention and detection capability along with fully automated response actions and a full 24x7 MDR service to boot. If I were suffering from a lack of cybersecurity resources, as most companies are, my first call to improve my situation would be to Cynet.
THN
#osutayusuf
- Get link
- X
- Other Apps
- Get link
- X
- Other Apps

Comments
Post a Comment